Recently, we had a requirement to put some files into a storage account, and to do that, for security reasons, we had to use Logic Apps Managed Identity to connect to the storage account. At first glance, this is a relatively simple requirement:
- Logic Apps has a Blob Storage Account API Connection that we can use.
- And Blob Storage Account API Connection supports Logic Apps Managed Identity.
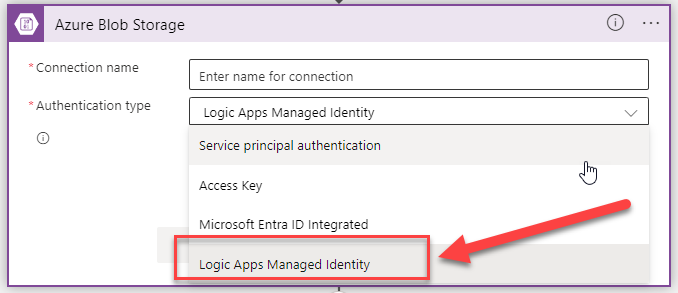
Of course, you must enable managed identity authentication in your Logic App to use it. Then, you must grant the required access to the identity in the target resource for it to work properly.
The problem is that when you create a new connection, it will give default names like azureblob. We always change those names to have a proper naming convention, which means that when we deploy our Logic App, this will create a new API Connection with the proper name, but it will create the API Connection with default configurations using a Storage Account Access Key:
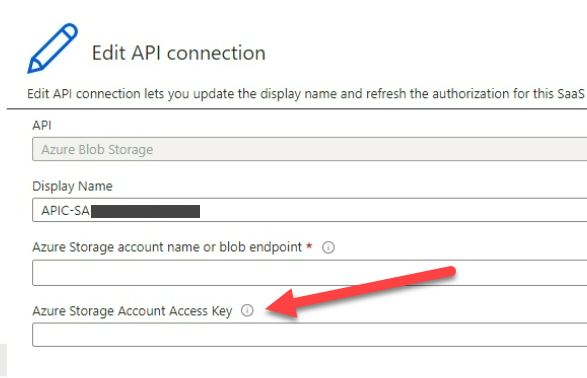
And even if you try to modify that in the Azure Portal… you cannot.
On one side, we were trying to apply good naming conventions, and on the other side, this was causing huge issues while developing inside Visual Studio.
The most important question was: How do we define the API Connection, in this case, the Blob storage, to use Managed Identity in our ARM template file inside Visual Studio? This is necessary for the CI/CD to work properly across different environments.
Setting up an API connection to use Logic Apps Managed Identity inside Visual Studio 2019
You need to perform a few steps inside your Logic App ARM template file for this to work. The first thing you need is:
- Open the LogicApp.json file (ARM Template) in code view (not with the Logic App Designer)
- Then, clean unnecessary API Connection ARM parameters settings. By default, when you create the Blob connection, even if you choose to use Logic Apps Managed Identity, it will create in the ARM Template file the following ARM Parameters:
- azureblob_1_Connection_Name
- azureblob_1_Connection_DisplayName
- azureblob_1_accountName
- azureblob_1_accessKey
- azureblob_1_authType
- azureblob_1_privacySetting
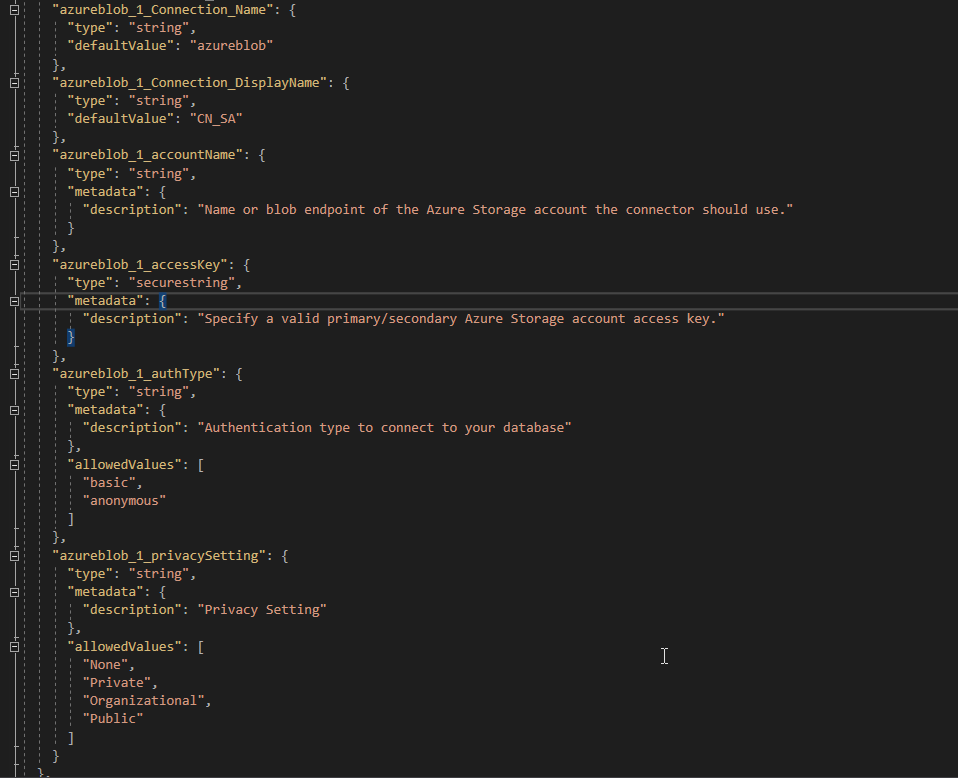
- Delete them all, with the exception of the connection name and display name. You can take this opportunity to rename them… since I hate everything that has _1_. And give the connector a proper name!
- azureblob_1_Connection_Name
- azureblob_1_Connection_DisplayName
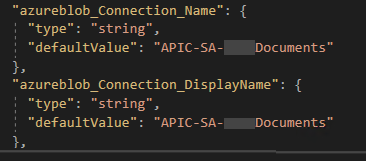
- In order to rectify the errors caused by us removing the previous ARM parameters. Scroll down to the end of the ARM Template file, most specifically into the resources section in the [parameters(‘azureblob_1_Connection_Name’)] (type “type”: “MICROSOFT.WEB/CONNECTIONS”).
- There, you will see the configuration of the API Connection, in this case, our Azure Blob connection, using some parameters that we deleted.
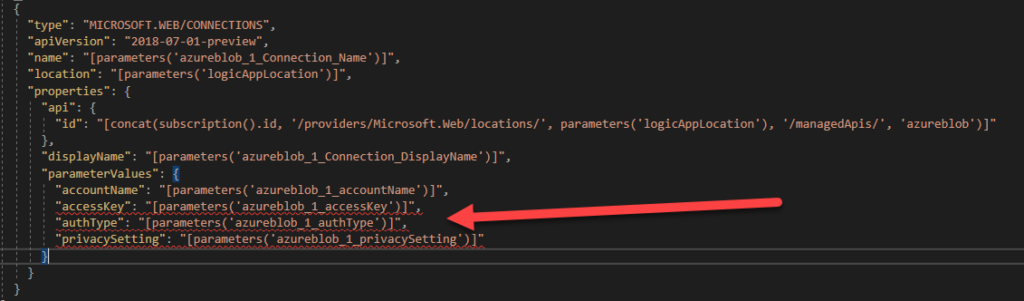
- Replace that Azure Blob connection configuration with this one:
{
"type": "MICROSOFT.WEB/CONNECTIONS",
"apiVersion": "2016-06-01",
"name": "[parameters('azureblob_Connection_Name')]",
"location": "[parameters('logicAppLocation')]",
"kind": "V1",
"properties": {
"displayName": "[parameters('azureblob_Connection_DisplayName')]",
"statuses": [
{
"status": "Ready"
}
],
"customParameterValues": {},
"api": {
"id": "[concat(subscription().id, '/providers/Microsoft.Web/locations/', parameters('logicAppLocation'), '/managedApis/', 'azureblob')]"
},
"testLinks": []
}
Finally, we need to configure our Logic App to use Managed Identity and also configure the connection con. To do this, we need to:
- Inside the ARM Template file, access the Logic App code present inside the resources section and add an identity configuration below the tags element:
"identity": {
"type": "SystemAssigned"
},
- Finally, we need to set the connection authentication type to be Managed Service Identity. And to do that, we need to:
- Inside properties > parameters element, add the following configuration
"$connections": {
"value": {
"azureblob": {
"id": "[concat(subscription().id, '/providers/Microsoft.Web/locations/', parameters('logicAppLocation'), '/managedApis/', 'azureblob')]",
"connectionId": "[resourceId('Microsoft.Web/connections', parameters('azureblob_Connection_Name'))]",
"connectionName": "[parameters('azureblob_Connection_Name')]",
"connectionProperties": {
"authentication": {
"type": "ManagedServiceIdentity"
}
}
}
}
}
After those changes, I was able to properly deploy the API Connection using Logic App Managed Identity, and the Logic App was properly configured.
May the 4th be with you!

Hope you find this helpful! If you enjoyed the content or found it useful and wish to support our efforts to create more, you can contribute towards purchasing a Star Wars Lego for my son!


